This article has been just updated: January 16, 2024
 You may have heard about the Tor browser. It has been prominently featured in news stories over the years as a portal to all of the evils that lurk in the part of the Internet known as the dark web. In fact, mention of the Tor browser is almost synonymous with accessing the dark web in some circles.
You may have heard about the Tor browser. It has been prominently featured in news stories over the years as a portal to all of the evils that lurk in the part of the Internet known as the dark web. In fact, mention of the Tor browser is almost synonymous with accessing the dark web in some circles.
The Internet that you can access by using search engines like Bing or Google is known as the surface web. The surface web comprises only about 4% of the web’s content. The rest of the Internet is made up of the deep web and the dark web. Information in the deep or dark web is only accessible through specialized browsers. The dark web is notorious for hosting sites that engage in a wide range of illegal activities.
While you can definitely use the Tor browser to connect to sites in the deep or dark web, that is not the only reason to use the application. We are going to attempt to dispel some misconceptions regarding what Tor is and how it can be used. Here are the answers to seven questions you may have if you are considering using this browser.
#1 What is a Tor Browser?
Tor is an open-source web browser that is free to download and use. It is available for Windows, Linux, Android, and you can even get a Tor browser for your Mac. The word Tor stands for the onion router. The use of the onion metaphor will become more evident as we explore how Tor works.
There is also a Tor network which is made up of many volunteer computers which are all running a specialized server application.
The Tor browser can provide a user with anonymity while accessing the Internet as well as allowing them to use special services which are features of the Tor network. Tor browser bundles in many languages are available from the Tor download site.
#2 What Problem is Tor Designed to Solve?
Tor is designed to foil Internet monitoring known as traffic analysis. This monitoring technique focuses on the headers of the data packets that make up messages sent over the Internet.
Even if you encrypt the data portion of your data transmissions, information such as source, destination, size, and other items can be determined by studying the headers. Through an analysis of message headers it can be determined which parties are communicating with each other and the size of the transmissions they are conducting.
Divulging this kind of information to anyone who might be monitoring the network you are communicating on may not be to your liking. In some cases, it can pose real financial or physical danger by revealing your identity to advertisers or governmental agencies. Repressive governments may harass individuals based on their online communication patterns.
Tor is designed to resolve the issue of traffic analysis by keeping your Internet communications anonymous.
#3 How Does Tor Work to Ensure Anonymity?
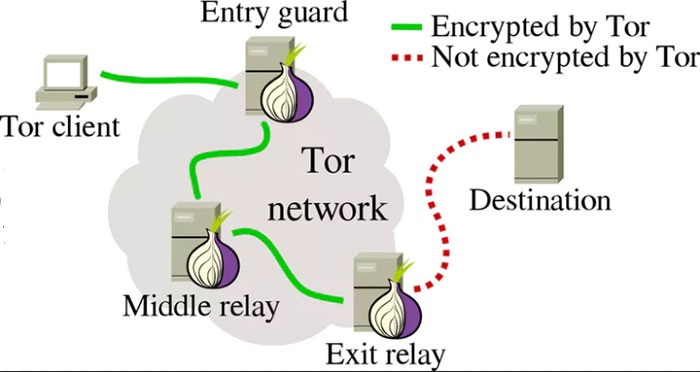
Tor creates a distributed, anonymous network in order to preserve the anonymity of its users. Your web traffic is routed through the Tor network (onion router), effectively anonymizing it. In simple terms, the Tor browser connects to a publicly listed entry node, forwards your data through randomly selected relays, and then sends it out through an exit node.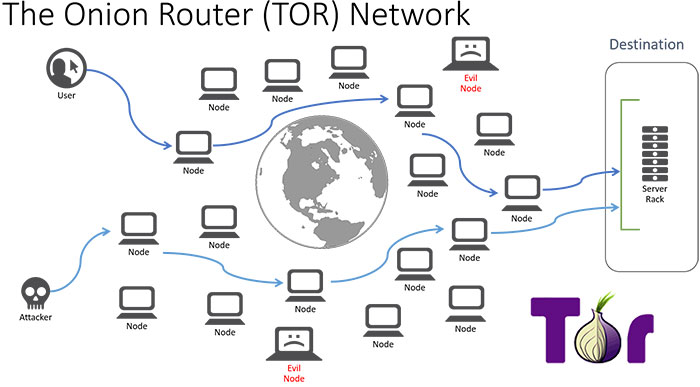
Diving a little deeper, we find that the private network pathway is built incrementally using encrypted connections through network relays. The path is extended one hop at a time, with a relay only knowing which relay provided data and which relay will be the receiver. No relay knows the complete path. In this way, the anonymity of the sender is maintained.
Tor can be used with any type of TCP data and is usually used for data sent over the Internet. It cannot be used for UDP data.
#4 How is Tor Used?
Tor is used for a variety of reasons, not all of which are legal. Some specific uses of Tor are:
- Accessing .onion websites. Many organizations such as the New York Times or Facebook have alternative .onion sites. You cannot use your regular browser to connect to these sites. Using the Tor browser allows you to access these sites anonymously, perhaps subverting government censorship.
- Tor can be used as an alternative to a VPN when keeping your browsing history confidential is desired. It will keep your online movements private without the need to install an additional software package.
- Obtaining legitimate information that is located on the deep web.
- Connecting to sites on the dark web for the purpose of engaging in illegal activities. This is not recommended and we discourage individuals from using Tor in this way.
#5 Who Uses Tor?
Tor is used by many individuals as well as government agencies. Here are a few examples:
- Journalists use Tor to protect their privacy and safety and subvert repressive censorship.
- Law enforcement officers use Tor to conduct online surveillance, conduct sting operations and set up anonymous tip lines.
- Activists and whistleblowers can make their reports anonymously using Tor.
- Regular people use Tor to keep their online activities private or when researching sensitive subjects.
For more detailed information on who uses Tor, check out torproject.org.
#6 Is it Legal and Safe to Use Tor?
Tor is legal to use on your computer and some users may prefer it over other web browsers. It does offer you the ability to access many more websites than a more traditional browser such as Chrome or Firefox. Those applications limit connections to sites on the surface web. If you want to extend the breadth of your Internet access to the deep or dark web, then the Tor browser may be just what you need.
Legality and safety can be slippery subjects, and while simply downloading and using Tor may be safe and legal, using it in certain ways crosses the line and exposes you to serious consequences. It’s like owning a chainsaw. You can use it as intended, safely and legally. Or you can be reckless and dangerous, resulting injury to your self or others.
The key is where you go and what you do while using the Tor browser. Stay away from illegal sites and be wary of malware that may be lurking on websites just waiting for an unsuspecting user to come along. If you follow those guidelines, you should have no problem using the Tor browser.
#7 Are There Any Issues Associated With Using Tor?
Slow performance is the major problem reported by users of Tor and may be enough of a reason to dissuade you from using this application. Sending your data through all those relays to preserve anonymity takes time and slows down your connection.
Simply using the tool may raise red flags to authority figures who have access to your computer system. For instance, if you use Tor on a work computer you may be suspect as a whistleblower. Management may distrust your desire to have your communication remain anonymous. Government agencies may take a closer look at individuals who have Tor installed on their computer.
There you have it. You can now make an informed decision regarding Tor and decide for yourself if it is right for your computing needs.
FAQ
What exactly is the Tor Browser?
The Tor Browser is a free, open-source web browser that prioritizes privacy and security by routing your internet traffic through a global network of volunteer-operated servers. This process, called onion routing, helps protect your anonymity online by encrypting your activities and disguising your location and usage from anyone conducting network surveillance or traffic analysis.
How does Tor ensure anonymity?
Tor ensures anonymity by utilizing a distributed network of relays run by volunteers around the world. When you use Tor, your internet data is encrypted and sent through this network, bouncing through multiple relays before reaching its final destination. Each relay only knows the address of the previous and next relay, making it extremely difficult to trace the path or uncover a user’s identity.
Is there a cost to use the Tor Browser?
No, the Tor Browser is completely free to download and use. It is maintained by a nonprofit organization called the Tor Project, which relies on donations and grants to support their work in providing digital privacy and freedom. You can find the browser on their official website.
What operating systems can run the Tor Browser?
The Tor Browser is available for Windows, macOS, and Linux operating systems. It can be easily installed just like any other browser and doesn’t require any special hardware or complex configurations to run.
How can I download and install the Tor Browser?
You can download the Tor Browser from the Tor Project’s download page. Choose the version that’s compatible with your operating system, then follow the standard installation process for your system. Once installed, you can start using Tor right away for enhanced privacy online.
Is using the Tor Browser legal?
Yes, using the Tor Browser is legal in most countries. It is a legitimate tool for privacy-minded individuals, journalists, activists, and anyone who wants to protect their online identity. However, some countries with strict internet censorship may restrict or ban its use.
Can I access regular websites using the Tor Browser?
Yes, you can access most regular websites using the Tor Browser. However, because traffic is routed through multiple relays, loading times may be slower. Additionally, some websites may block traffic from Tor due to abuse concerns.
What are .onion sites and how can I access them?
.onion sites, also known as hidden services, are websites that offer anonymity for both the visitor and the website itself, and they can only be accessed via the Tor network. To access them, you’ll need a .onion URL, which you can enter into the Tor Browser just like a regular web address.
Is it safe to use the Tor Browser for sensitive activities?
While the Tor Browser significantly enhances privacy, it’s important to follow best practices such as not sharing personal information, being wary of downloads, and using secure HTTPS connections when available. No privacy tool is 100% foolproof, so being cautious with sensitive activities is always recommended.
Does the Tor Browser store my browsing history?
No, the Tor Browser is designed to automatically clear your browsing history and cookies after every session. This helps protect your privacy by preventing subsequent users of the same computer from discovering your online activities.
Can I use browser plug-ins and extensions with the Tor Browser?
It’s generally not recommended to install additional browser plug-ins and extensions in the Tor Browser as they could compromise your anonymity by leaking personal information. The browser is pre-configured with privacy-focused features, and modifications can reduce its effectiveness.
Is the Tor Browser different from a VPN?
Yes, the Tor Browser is quite different from a VPN. While both tools aim to protect user privacy, a VPN encrypts all of your internet traffic and routes it through a server operated by the VPN provider, whereas Tor encrypts your traffic and randomly routes it through a network of volunteer-operated servers. In addition, VPN providers can potentially log your traffic, whereas Tor’s decentralized nature makes tracking by a single entity more challenging.
How do I update the Tor Browser?
Updating the Tor Browser is simple. When an update is available, you’ll be notified through the browser, and you can follow the prompt to update it. You can also check for updates manually by clicking on the hamburger menu (≡) in the top right corner, navigating to ‘Help,’ and then selecting ‘About Tor Browser.’
Can I use bookmarks in the Tor Browser?
Yes, you can use bookmarks in the Tor Browser almost the same way you would in any other browser. However, it’s worth noting that over time, a large collection of bookmarks could potentially be used to identify you, so use this feature with caution.
How does Tor protect against malware?
Tor cannot protect against malware on its own, but by using the Tor Browser, you gain some protection as it isolates each website you visit so third-party trackers and ads can’t follow you. Any downloaded files, though, should still be treated with caution and scanned for malware with antivirus software.
Can Tor Browser be used on mobile devices?
Yes, there is a version of the Tor Browser available for Android devices. iOS users can use the app ‘Onion Browser,’ which is endorsed by the Tor Project, as their official mobile browser is not available for iOS devices.
What kind of internet activities can I perform on the Tor Browser?
You can perform most standard internet activities on the Tor Browser, such as browsing websites, checking email, and accessing social media. However, certain high-bandwidth activities like streaming video might be slow due to the nature of Tor’s network routing.
Is it advisable to access personal accounts through the Tor Browser?
Accessing personal accounts over the Tor Browser can be a trade-off. While it masks your IP address, it might also trigger security alerts from service providers that detect the login as unusual activity, as it may appear to be coming from a foreign or unexpected location. Always ensure you’re using HTTPS for an encrypted connection to minimize risks.
Can businesses make use of the Tor Browser for their operations?
Businesses can utilize the Tor Browser for research or for ensuring the privacy of communication, especially when it comes to protecting sensitive information or intellectual property. However, due to its speed and potential legal considerations, it’s important to weigh the pros and cons for business use cases.
What measures can I take to enhance privacy while using the Tor Browser?
To enhance your privacy while using the Tor Browser, avoid using plugins, keep the browser updated, use HTTPS versions of websites when possible, don’t download and open documents while online (especially those handled by external applications), and avoid enabling scripts on questionable websites.